Masa Hashiguchi, Interfocus’s Lead Solutions Engineer, continues to share best practices for IT security, derived from the network infrastructure and IT operations across our 10,000 clients around the world.
In my last Technology Tip blog, I shared tips for performing secure backups to strengthen your stance against data accidents. This time I am focusing on how to identify file extensions and what to look for before you open a potentially harmful file. File extension examination is well-known and understood, which might lead you to believe that hackers know all the ways around it. But they can get sloppy, so regular analysis of file extensions is still effective in identifying a disguised malicious file.
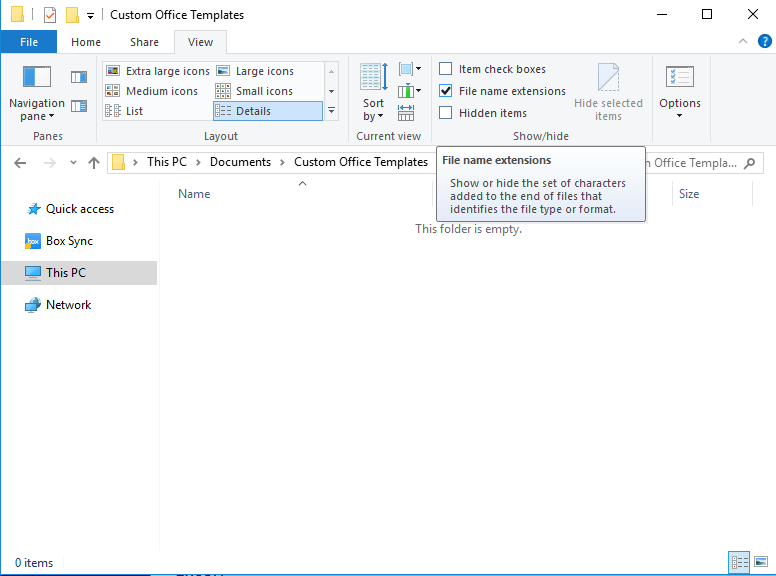
To turn on the “File name extensions” option in Windows 10, open File Explorer, choose View, and select File name extensions. On older versions of Windows, you may find this option by navigating to the Tool option of File Explorer.
Simple enough. Check “File name extensions.”
Here are a couple of examples of how file extension review can identify malicious files.
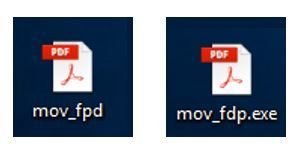
Example 1: In this example, a malicious file is disguised to appear, at first glance, as a harmless PDF document. In the image below, both icons represent the same file. The left-hand image shows how the file will appear with the File name extensions option turned off. It looks like a PDF. But when you turn on the File name extensions option, you immediately see, in the right-hand image, that this is a portable executable file and clicking on it will launch a potentially harmful process.
Example 1: Without and with file extensions
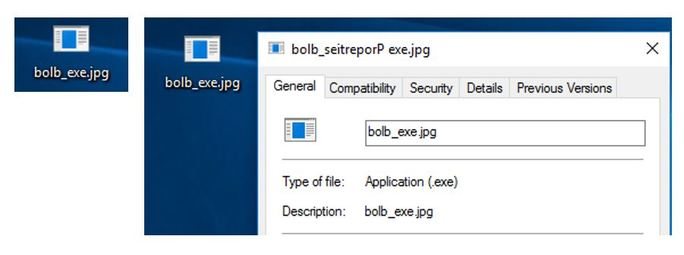
Example 2: This example illustrates a potentially harmful file disguised as a JPG. In the image below, the left-hand item shows what appears to be a graphic file with a *.JPG extension. The creator of this file, however, used a Right-to-Left Override (RLO) to disguise Unicode control code in the middle of the file name. Clicking on this icon will launch the executable bolb_seitreporP.exe and off it will go.
Example 2: Right-to-Left Override of the filename
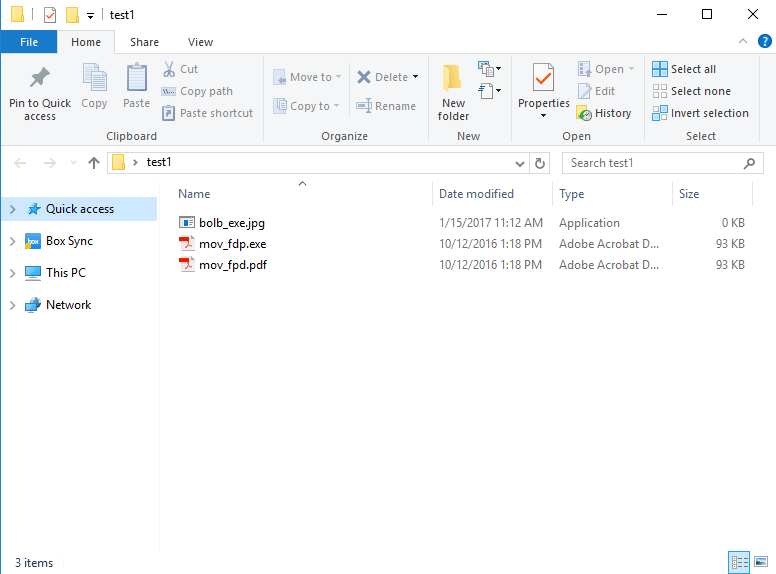
To prevent this, you should always use File Explorer to check the file type before opening any file.
With the correct options set, File Explorer will display file type information.
Simple! Once you have set these settings, it’s easy for you and your team to do this quick check and save your network and your data from potential harm. Make this part of your IT best practices.
There are many other resources available on this topic. Check out one of my favorite posts, which also covers Right-to-Left Override: https://blog.malwarebytes.com/cybercrime/2014/01/the-rtlo-method/