We are pleased to introduce a new component to our blog, wherein Masa Hashiguchi, Interfocus’ Lead Solutions Engineer, shares best practices for IT security, derived from the network infrastructure and IT operations across our 10,000 clients around the world.
Do you have a backup strategy for 2017? If not, you should. Incorporating backup strategies into your daily routine strengthens your defense against ransomware and other data accidents.
Latest research reveals that 70 percent of ransomware-impacted businesses have had no choice but to pay the ransom demands in order to re-establish their business processes and restore their data.[1] There are a variety of tools available to assist with decrypting the affected files, but having a backup copy of your files will save you time restoring your data and eliminates the need to navigate that difficult process. Backup activity should be implemented by both IT Managers and end users alike. Having access to backup files of important data provides strong resilience against attacks.
What is the best backup strategy to implement? General practice suggests storing your files in several backup different formats [2]. Although USB thumb drives are readily available and are a decent solution for storing files, most professionals agree that they should not be your sole source of storage. While they are definitely “better than nothing”, thumb drives should only represent a small portion of your backup routine. To be most effective, your backup strategy should include at least two (or three) backups formats.
Here is my personal backup routine, derived from best practices observed across organizations large and small:
- File backup –USB thumb drives are readily available and an easy solution for file backup. You should note that not all USB thumb drives are created equally. To prevent data theft, consider using a password encrypted USB, like SecureUSB. There is also a practice to disable autorun features (Autorun.inf) that will prevent infected USBs from immediately attacking computers when they are plugged in.
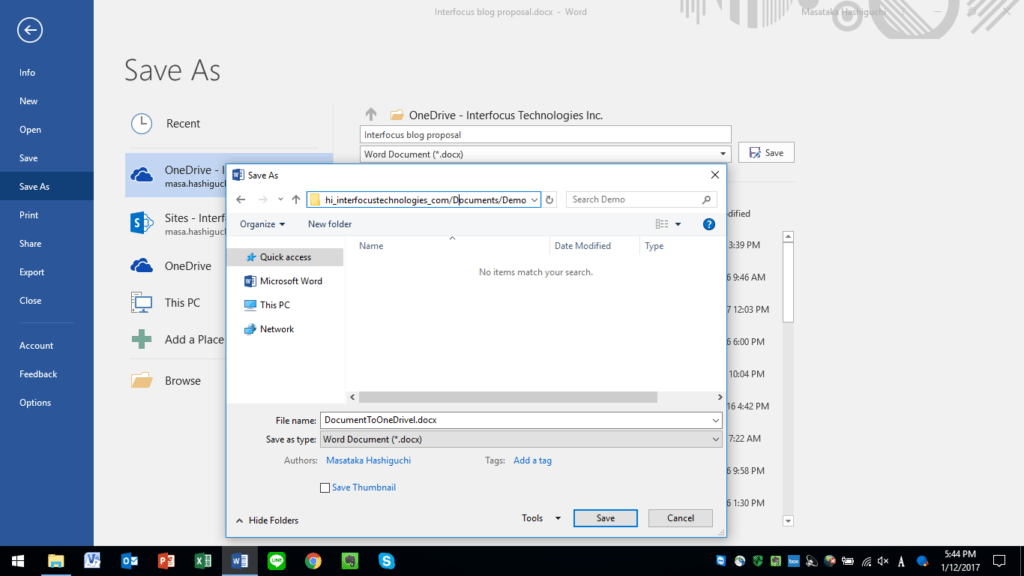
- Office 365 OneDrive for Business – Although OneDrive is not technically a backup solution, I use it to save and store files into the cloud. The seamless integration between Office and OneDrive makes it so easy to store files that I often forget to save the files locally! As an added benefit, cloud storage allows me to access my files from different devices. Again, the key in this process is to have a variety of reliable places to store important data so that if one area gets attacked, you still maintain a safe copy.
A familiar “Save As” prompt to save file to OneDrive. Very easy and seamless.
- The Windows Backup Feature – Windows provides two very powerful backup options:
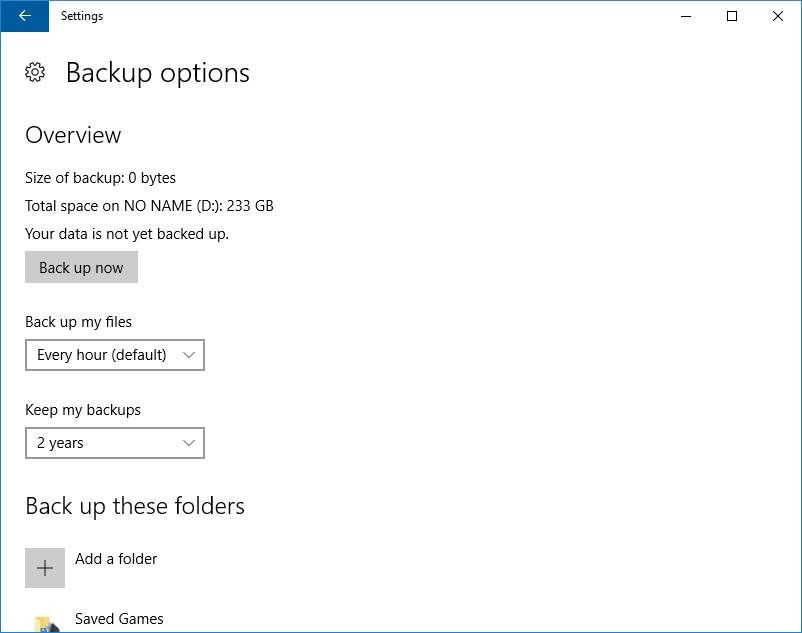
- File History – The newer Windows “Time Machine” feature, like the common Mac backup feature, can be used to backup local files. The screen shot below displays various options in this process.
Time Machine backup on Windows! Woohoo - System Image Backup – This feature can be used to back up EVERYTHING including your operating system, installed applications and configurations, besides files [3].
- File History – The newer Windows “Time Machine” feature, like the common Mac backup feature, can be used to backup local files. The screen shot below displays various options in this process.
It is important to note that after completing the backup copy process, I usually unplug my USB device. Why? Based on best practices recommended by security professionals, it’s important to unplug the external drive immediately after completing a backup as there is a possibility that some malware/ransomware will attack even the external drive.
What is the bottom line for backing up files? You can’t survive without a solid backup strategy that includes backing up files in several ways. Don’t trust only one solution!
Note: If you are using a company-issued laptop, consult your IT department to find out their best and preferred backup strategy. Feel free to share this blog post with them, to assess whether there is room for improvement from today’s operations to best practices for network security!
[1] https://www-03.ibm.com/press/us/en/pressrelease/51230.wss 14 Dec 2016
[2] http://www.hanselman.com/blog/TheComputerBackupRuleOfThree.aspx
[3] https://www.howtogeek.com/192115/what-you-need-to-know-about-creating-system-image-backups/